As well as turning leaves and pumpkin carving, October means it’s time for International Cybersecurity Awareness Month!

Fig 1: Cybersecurity Awareness Month is observed internationally, including in Canada, the US, and Europe.
With much of the world working remotely and companies making rapid technological adaptations, there’s no better time to have a conversation around information security.
Let’s be honest though, information security isn’t the most exciting topic. It can seem impossibly technical, overwhelming, or just be dismissed as “the IT guy’s job.”
However, to develop a resilient business with a strong information security culture, it’s vital for everyone to be involved.
In this blog post, we’ll break down this daunting topic - or you can skip ahead to some practical tips on how to keep your valuable information secure.
Check out our brief video overview here and enjoy the read!
Why information security matters in the AEC industry
It’s no secret that construction data is one of, if not THE most valuable asset for a company in the AEC industry.
Cybersecurity expert at Talatek,
interviewed for Construction Dive.
With a high volume of information exchange, model sharing, and high-stakes confidentiality, the construction industry is particularly vulnerable to breaches of security. According to the Construction, Engineering and Infrastructure executives surveyed for the 2019/20 Kroll Global Fraud and Risk Report, the construction industry has been hard-hit by leaks of internal information, with 45 percent of firms reporting significant effects within the last year (vs. 39 percent for all industries).
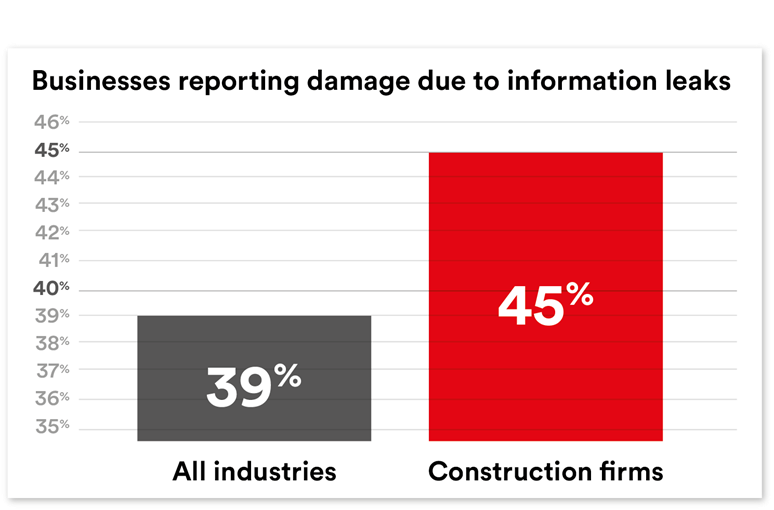 Fig 2: The 2019/20 Kroll Global Fraud and Risk Report indicates that the construction industry is high risk for internal information leaks.
Fig 2: The 2019/20 Kroll Global Fraud and Risk Report indicates that the construction industry is high risk for internal information leaks.
Clearly, failing to invest in information security is not worth the cost, loss of client trust, and reputational damage. On the plus side, a strong information security culture can be a winning selling point, and inspire the trust of your clients and partners.
Read on for some practical tips on what you can do to keep your data secure.
Your Software Security Inspection Checklist
Nobody’s tech stack is longer than an AEC professional’s. This inspection checklist takes you through the questions you want to be able to answer about the software you’re using every day, in order to keep your information secure.
Your home inspector does it before you invest in a home. So why shouldn’t you do it when considering a piece of software?
Cloud-based data security
Disaster recovery - is there a plan in place?
- Geo Redundancy is the capacity for a software to replicate the data on different servers in multiple locations, to provide a seamless transition in case of a disaster happening in the main servers’ location such as a fire, earthquake, etc. It’s definitely something you want to have!
Is your data protected with backups?
- Make sure that there are regular backups made of your data to avoid data loss in case of a breach on the software solution’s systems.
Is the data encrypted?
- It is essential that sensitive information is sent on the Internet in an encrypted format (through TLS secure protocol, which in the context of Web application, is called HTTPS).
- For very sensitive information, it is also well advised to make sure that the data that is stored at rest, which means, on the data servers’ storage, is encrypted.
Where are the data servers hosting customer data located?
- Some countries have data residency requirements that oblige organizations to host data locally, especially in the public sector.
Compliance with international security standards
Does the platform have a globally recognized information security certification? (e.g. ISO 27001, SOC 2 Type II).
- Certifications such as ISO 27001 ensure that a software reaches a high standard of security including watertight policies, internal and external audits, risk assessment and risk management procedures, online payment security standards, and more.
*Important! Make sure that the organization itself is certified, and not just the server where the software is hosted. This is a common cybersecurity myth and can be a costly mistake.
Is the company GDPR compliant?
- While not every country requires the level of stringency outlined in the European General Data Protection Regulation law (GDPR), choosing to follow these guidelines proves a high level of commitment to transparency and accountability with handling and protecting personal information.
Is the company open to questions?
- This final point comes down to soft skills, but it can be a powerful indicator of security how your software vendor reacts to questions, how accessible their support teams are and how open lines of communication are with their internal security team? Try to probe around and assess the general level of openness and transparency.
Your 30 second cybersecurity tune-up
If you take nothing else away from this blog post, you can do these three things today to dramatically improve your level of cybersecurity:

Fig 3: Improving cybersecurity is something you can do right now. Don’t wait!
- Tighten up your password management
by using a password manager that saves you the hassle of creating – and especially remembering! – long, complex and unique passwords. When it comes to setting your master password, don’t underestimate the exponential security benefit of using a passphrase instead of a word:
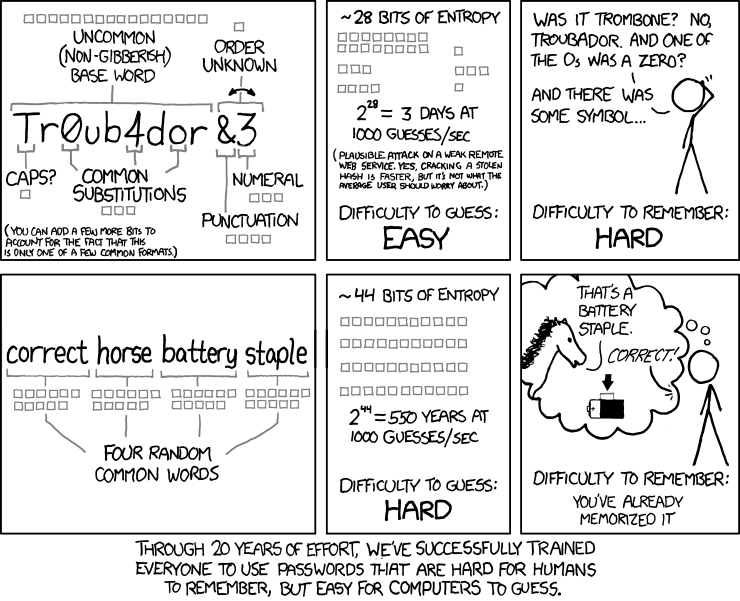
Fig 4: Here’s proof from XKCD Webcomic that a passphrase is exponentially more secure than a password.
- Put 2 factor authentication on your most critical accounts
such as your Google account, Microsoft account, or Apple account. You can check out this list of all 2FA compliant websites to see which accounts you can upgrade. - Educate yourself on email phishing scams,
which have seen a dramatic increase in 2020. Try out this quiz to see if you can spot when you’re being phished.
We hope you were able to find some practical take-aways that will help you tighten your belt when it comes to information security.
One final word? Keep it fun! Speaking of belt-tightening, here at BIM Track and BIM One, we’ve implemented a stringent Donut Policy for anyone who leaves their computer unlocked and unattended. 🍩

